January 2006 Show Summaries
| Show Summaries Below |
| January 25, 2006 January 18, 2006 January 11, 2006 January 4, 2006 |
| January 25, 2006 Show | AudioArchives TOP |
Our guest was Tony Bov, author of the just released book "Just Say No to Microsoft". From the Amazon.com description:
"Just Say No to Microsoft begins by tracing Microsoft's rise from tiny software startup to monopolistic juggernaut and explains how the company's practices over the years have discouraged innovation, stunted competition, and helped foster an environment ripe for viruses, bugs, and hackers. Readers learn how they can dump Microsoft products--even the Windows operating system--and continue to be productive."
- Author's web site www.tonybove.com
- Long list of alternative software from Tony Bove tonybove.com/getoffmicrosoft/home.html
- Book Publisher www.nostarch.com
For alternate operating systems, we discussed Macintosh machines (Tony's favorite) and Linux. Two obvious choices are Firefox to replace IE and Open Office to replace Microsoft Office. Tony mentioned a number of email programs that can replace Outlook Express and Outlook.
Michael asked about replacing the calendaring features of Outlook. Although Tony has no first hand experience with it, he suggested www.officecalendar.com or Mozilla's Sunbird www.mozilla.org/projects/calendar/sunbird.html. Tony pointed out that the hottest category in development these days is AJAX development -- web services that work with your browser, regardless of computing platform and, of course, independent of Office. He found of list of AJAX based calendars: www.techcrunch.com/2006/01/30/spongecell-an-ajax-calendar/
After the show a listener suggested this list of open source programs for Windows osswin.sourceforge.net
| January 18, 2006 Show | AudioArchives TOP |
Microsoft will port Virtual PC for the Mac to the new Intel based Macintosh machines. Virtual PC lets you run Windows, and thus all Windows programs, on a Macintosh. They will also continue to develop Microsoft Office for the Mac for at least the next five years.
New iMacs: with a 17 inch monitor for $1,300; with a 20 inch monitor for
$1,700.
New MacBook Pro laptops: with a 15 inch screen from $2,000 to $2,500.
Symantec, Kaspersky criticized for cloaking software January 12, 2006. ComputerWorld. Windows expert says antivirus firms have "no good justification" for rootkit technique
Alfred reported on his trip to the Consumer Electronics show.
In discussing Google's Gmail system, Michael pointed out that gmail users can create an unlimited number of thowaway email address. If, for example, your email address was "michael@gmail.com" , you could use
- michael+nytimes@gmail.com when registering at the New York Times' web site
- michael+ebay@gmail.com when registering at eBay
- michael+drugstore.com@gmail.com when registering at Drugstore.com
- etc. etc.
To the outside world each of these is a separate email address. However, to Gmail, they are all the same -- that is, they all end up in your single Gmail inbox. Should you start to get a lot of spam on one of these accounts, you can create a filtering rule to throw them away. Plus, you know who to blame for the spam.
Were you confused about the recent WMF problem in Windows? Steve Gibson has a free program that you can download and run on your computer to see if it is vulnerable to the WMF problem. www.GRC.com/miscfiles/KnockKnock.exe
Microsoft did not fix Windows 98 and Me. Users of these versions of Windows may want to install the WMF Patch by Paolo Monti. Use it at your own risk. Eset, the company that makes the NOD32 anti-virus software says "Customers running an up-to-date version of NOD32 are protected without having to take any special actions.".
On January 12th a serious bug in Apple's QuickTime software came to light. See
www.us-cert.gov/cas/techalerts/TA06-011A.html
| January 11, 2006 Show | AudioArchives TOP |
The show was pre-empted this week due to the Alito hearings.
Speaking of which, on January 10th, askSam released the transcripts from Judge Samuel Alito's confirmation hearing in a free, searchable askSam database. See: www.asksam.com/ebooks/Judge_Alito
This page contains links to the transcripts from Judge Alito's confirmation hearing as well as to his published opinions. You can search this information on the Web or download and search it on your own PC. The database will be updated each day during the hearings. Press release with more information: www.asksam.com/releases.asp
In addition, askSam has also prepared free searchable versions of other legislative and political texts, works of literature, and government reports, including:
- Judge John Roberts' Confirmation Hearing Transcripts
- Judge John Roberts' Published Opinions
- Intelligence Reform and Terrorism Prevention Act
- USA Patriot Act
- 9-11 Commission Report
- Sarbanes-Oxley Act
- HIPAA (Health Insurance Portability & Accountability Act)
- Basil II Accord
You can find more information on these and other files at: www.asksam.com/eBooks/
| January 4, 2006 Show | AudioArchives TOP |
IMPORTANT NEWS FOR ALL WINDOWS USERS
January 12, 2006. To verify that the official Microsoft WMF patch/fix
is installed on a computer, go to Add / Remove Programs applet in the Control
Panel (in XP you may have to check the box ‘Show updates’). Scroll down list of Windows updates
(in Windows 2000, they all start with "Windows 2000 Hotfix") and look
for KB912919. If it's there, the computer is safe.
January 10, 2006. The fix for the WMF bug can also be downloaded
directly without going through Windows Update
- For Windows 2000 Service Pack 4
- For Windows XP SP1 and SP2
- Direct links for the server and 64 bit versions of Windows are in Microsoft Security Bulletin MS06-001
January 5, 2006: Microsoft released their official fix for the WMF bug (more below) today. You can get the fix using Windows Update (update.microsoft.com). They originally said it would be released on January 10th, but then opted to release it early.
Install it now!
The bug fix is for Windows 2000 or Windows XP or Windows 2003 Server. If you are using Windows 98, 98SE or Me, no fix for you.
If you did not apply the unofficial patch that we recommended on last night's show, then this patch/fix applies just like any other, there is nothing special you need to do.
If you did apply the unofficial patch from IIfak Guilfanov (as we suggested), then it can be removed either before or after installing the official patch from Microsoft. The two can co-exist, but there is no need for the unofficial fix after the official fix has been installed. SANS suggests:
- Re-start Windows to clear any vulnerable files from memory
- Download and apply the official Microsoft fix using Windows Update
- Reboot (You will be prompted to reboot - it's required to finish installing the bug fix)
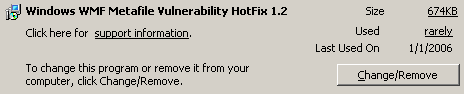
Uninstall the unofficial patch by using the Add/Remove Programs applet in the Control Panel. It should look like the picture at the right.- Reboot one more time just for good luck
Microsoft Security Bulletin Advance Notification January 5, 2006. That original release date? Uh, never mind. And speaking of dates this is from January 2006, not from January 2005 as it says.
Microsoft Security Bulletin MS06-001 Vulnerability in Graphics Rendering Engine Could Allow Remote Code Execution. January 5, 2006. Says why there is no patch for older versions of Windows. At least it gives Microsoft's public reason. Michael suspects the real reason is that they make no money off people using older versions of Windows and would prefer they upgrade.
A simple and easy to understand explanation of the WMF problem from Cert.org
Vulnerability Note VU#181038
Microsoft Windows Metafile handler SETABORTPROC GDI Escape vulnerability
January 4, 2006: A very serious bug in Windows was discovered on December 28th. This is arguably the worst problem that Windows has ever had.
Like many other Windows bugs, this one allows a bad guy to run a program on your computer and infect it with all sorts of malicious software. You don't have to do anything wrong to get infected. All that is necessary is viewing a WMF formatted file. Thus, just by looking at a web page (with any web browser) or just by reading an email message (without opening any attachments) you can get infected.
This bug is currently being exploited left and right. And it gets worse.
You're not even safe if you avoid every .WMF file ever created (if you work somewhere that is blocking WMF files in their firewall, it's a false protection). A malicious WMF file can be renamed with a different image file extension and still be processed by Windows in such a way that your computer can get infected. In other words, any image file (GIF, JPG, BMP, PNG etc.) could infect your computer! Even if the image is embedded in a Word document.
And if you get infected, there is no cure.
Mikko Hypponen, chief research officer at anti-virus and security firm F-Secure said "The potential for problems is bigger than we have ever seen. We estimate 99 percent of computers worldwide are vulnerable to this attack." It could be the worst Windows bug ever.
The bug exists in all versions of Windows, even back to Windows 3.0 from
1990 according
to F-Secure. Windows XP SP2 with all the latest patches applied is
vulnerable. Even the server versions of
Windows are vulnerable. That said, Windows XP and Windows Server 2003 are
the most vulnerable because they have a default file association for WMF files.
In a vanilla install of older versions of Windows you can't read WMF files. On
the other hand, Windows 2000 (and maybe older versions too) becomes vulnerable if
you have installed a third party image handling program. There is a safe
tester program that reports if your copy of Windows is vulnerable to this
problem (more...).
Major Revision In Vulnerable System List
by Larry Seltzer January 3, 2006
Not that it matters, but the problem is more of a design flaw in WMF files rather than a bug. That is, the WMF files are working the way they always did, they way they were designed, it's just that bad guys are now exploiting their insecure design.
Microsoft has no fix for the problem but expects to issue a fix on January 10, 2006. For now, they offer a work-around, but it protects you only some times, not all the time. Steve Gibson said it "provides very little protection."
The best protection is provided by a patch created by IIfak Guilfanov. We suggest applying the patch, which you download as an EXE file either from Mr. Guilfanov's web site www.hexblog.com or from SANS (version 1.4 of patch). Just run the file to install the patch, the process is fairly straightforward. The patch works on Windows 2000 and XP. If you are using Windows 95, 98, ME or NT4, no patch for you.
This patch is a temporary stop-gap. When Microsoft issues their patch, then this one should be un-installed. It un-installs in the normal way: Control Panel -> Add/Remove Programs. It will appear in the list of installed programs as "Windows WMF Metafile Vulnerability HotFix".
For an excellent explanation of the problem and the patch, read what Steve Gibson has to say in the Security Now! section of his web site.
- Excellent FAQ on the problem
- The problem was initially discovered by Sunbelt Software which has been updating their blog at sunbeltblog.blogspot.com with the latest information. See Exfol/WebExt using WMF exploit on rotational popups
- Patch Tuesday? That's the day after Public Relations Nightmare Monday, right? January 4, 2006. Lots of criticism of Microsoft.
- Patching Up Windows January 4, 2006. Associated Press. More criticism of Microsoft. "Microsoft's delay is inexcusable ... There's no excuse other than incompetence and negligence.''
- Windows metafile hole requires unofficial patch by Brian Livingston of Windows Secrets. January 4, 2006
- Trojan delivers unwanted gift to Windows PCs CNET News.com December 28, 2005.
- Microsoft's two cents: Microsoft Security Advisory (912840) Vulnerability in Graphics Rendering Engine Could Allow Remote Code Execution.
According to Steve Gibson (link above), WMF files can contain scripts (a type of computer program) that contain instructions to Windows to do things like drawing circles and squares. When there is an error in the drawing process, Windows executes an error routine. Oops. Now the bad guys make the WMF drawing process fail immediately and thus get Windows to do their dirty work and run a program. Not an error routine, but any program. Even a malicious one.
In one instance a computer was infected just by downloading a WMF file from a Command Window without ever viewing the file. The culprit in this case was Google Desktop which automatically indexes new files. This automatic background indexing of the bad file caused the infection.
Note that a lone programmer working on his own, for free, quickly did what Microsoft, with thousands of programmers in their employ, didn't. Mr. Guilfanov created and distributed his patch before Microsoft could even come out with a guess for when their fix would be available.
History: In early November 2005, Microsoft issued a bug fix for a different problem in the rendering of WMF files. That bug too would allow your computer to be infected just by viewing a maliciously designed WMF file. It took Microsoft seven months to issue the bug fix. See Critical Windows Patch Fights Takeover Attacks in eWeek magazine from November 8, 2005.